 |
 |
Help with Windows malware
|
 |
|
 |
|
Senior User
Join Date: Apr 2003
Status:
Offline
|
|
Hi, I use a Mac at home, but unfortunately, my work PC (windows XP) has contracted a form of the "Antivirus 2010" virus. Symptoms include false warning messages, periodic popups, and inability to run .exe's.
I have downloaded the free versions of Malwarebytes and SuperAntiSpyware, but whenever these programs run for a few seconds, the virus terminates them and changes the permissions.
I can fix permissions when I use "cacls" command on those particular .exe's from the command prompt, but once those apps open, they terminate again and the cycle continues.
Any advice on how to get rid of this clever piece of malware?
Many thanks.
|
|
|
| |
|
|
|
 |
|
 |
|
Grizzled Veteran
Join Date: Jul 1999
Location: FL Cape
Status:
Offline
|
|
My go-to antispyware has always been Spybot S&D. It can scan on boot to remove more persistent problems.
Lavasoft Adaware and Trend Micro Hijackthis! have been useful to me in the past as well.
|
|
|
| |
|
|
|
 |
|
 |
|
Administrator  Join Date: Apr 2001
Location: San Antonio TX USA
Status:
Offline
|
|
This piece of digital filth needs to be stuffed up the writer's ...... Well anyway. There are a lot of ways to do the removal, and most of the automated ones are susceptible to the malware's self-defenses.
Read the process at Windows XP/vista Blog, which provides a manual method of removal. Basically you'll kill the processes the crap uses, then you'll delete its files, then you'll remove its registry entries. After you've killed the processes, the Malwarebytes app should get the rest of the job done, but manually check that all the files and registry entries are gone.
And just to keep things neat, I'm going to move this thread to the Alternate OS forum, where it will also help others who run Windows on their Macs.
|
 Glenn -----OTR/L, MOT, Tx
Glenn -----OTR/L, MOT, Tx
|
| |
|
|
|
 |
|
 |
|
Moderator Emeritus
Join Date: Apr 2005
Location: Cambridge, UK
Status:
Offline
|
|
For a start, this should be in Alternative OS - we'll do the housekeeping later. We must have been typing at the same time-I got it moved after I finished my post.  Glenn Glenn
This is one of the nasties, easily contracted by performing an innocent Google search, while using Internet Explorer.
What you first need to do is identify the name of the program running and stop it.
If you can find the shortcut for this application, that will sometimes be on the desktop or in the start menu, you can view the properties of the file and look at the 'target' path, to find which folder the malware is stored in and what its filename is.
Sometimes it can be called av.exe, avp.exe or something else such as 419283.exe. You can try and end the process by using task manager - if you can open it, otherwise move on.
The 'application' can sometimes be found under
Code:
C:\Documents and Settings\<User>\Local Settings\Application Data\<interestingly named folder>
or
Code:
C:\Documents and Settings\<User>\Application Data\<interestingly named folder>
You may need to turn on 'show hidden files and folders' and uncheck 'hide protected operating system files' from the Tools menu > Folder Options > View tab.
We need to delete these folders, which we can do when the application is stopped. If you can't stop it, boot into Safe Mode, by pressing the F8 button when the computer starts, this prevents un-needed applications from loading (including the malware), then delete the folder.
Next, click Start > Run > and type 'msconfig' without the quotes.
Find the filename of the nasty software we were looking for earlier and uncheck it - just to ensure that Windows won't try to start it.
Next, reboot back into Windows normally and run Malware Bytes on a full scan, having fully updated it before you begin. It could take hours, you MUST let it finish.
Repeat this process until it finds nothing else.
Next, download and run TDSSKiller - if it finds an infection - you must be careful.
The TDSS rootkit sometimes hides itself within important Windows system files, removing these can render the PC inoperable. Post the name here if applicable.
Instead of using TDSSKiller to remove the rootkit, if it's embedded in a windows system file - we may be able to replace it by using the files Windows has cached. We'd open a command prompt and run SFC /scannow.
Next, check your hosts file, if it has a long list of IP addresses and URLs, it has probably been modified by the malware. Empty the hosts file and replace it with the defaults:
Code:
# Copyright (c) 1993-2009 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
# localhost name resolution is handled within DNS itself.
# 127.0.0.1 localhost
# ::1 localhost
Lastly, go to Control Panel and Internet Options. Click the connections tab, then the lan settings button.
Uncheck any boxes to do with using a proxy server relating to 127.0.0.1.
Now, hopefully your PC is clean.
My suggestion for the future, install Firefox, stop using Internet Explorer and ensure that you always update Adobe Flash, Reader, Acrobat and Java.
(
Last edited by ghporter; Oct 16, 2010 at 05:59 PM.
)
|
|
|
| |
|
|
|
 |
|
 |
|
Senior User
Join Date: Apr 2003
Status:
Offline
|
|
Originally Posted by ghporter 
This piece of digital filth needs to be stuffed up the writer's ...... Well anyway. There are a lot of ways to do the removal, and most of the automated ones are susceptible to the malware's self-defenses.
Read the process at Windows XP/vista Blog, which provides a manual method of removal. Basically you'll kill the processes the crap uses, then you'll delete its files, then you'll remove its registry entries. After you've killed the processes, the Malwarebytes app should get the rest of the job done, but manually check that all the files and registry entries are gone.
And just to keep things neat, I'm going to move this thread to the Alternate OS forum, where it will also help others who run Windows on their Macs.
Thanks, ghporter. I think the link above may be incorrect...are you able to provide an updated link? Thanks
|
|
|
| |
|
|
|
 |
|
 |
|
Senior User
Join Date: Apr 2003
Status:
Offline
|
|
seanc, thanks for the reply. Ironically, I was using an updated version of Firefox when the virus appeared. Even more ironically, the site I was on was appleinsider.com!
I think I may need more guidance on how to identify this "interestingly named folder". It seems I can't proceed to the other steps until I identify the killer process. I looked in those two hidden folders you recommended as well as the Task Manager, but nothing really is catching my eye, although I am not too sure what to look for. Nothing appears with "av" or "419283".
Thanks again for the help.
|
|
|
| |
|
|
|
 |
|
 |
|
Senior User
Join Date: Apr 2003
Status:
Offline
|
|
|
|
|
|
| |
|
|
|
 |
|
 |
|
Moderator  Join Date: Feb 2006
Location: on the verge of insanity
Status:
Offline
|
|
|
|
|
I like my water with hops, malt, hops, yeast, and hops.
|
| |
|
|
|
 |
|
 |
|
Moderator Emeritus
Join Date: Apr 2005
Location: Cambridge, UK
Status:
Offline
|
|
Originally Posted by jszrules 
seanc, thanks for the reply. Ironically, I was using an updated version of Firefox when the virus appeared. Even more ironically, the site I was on was appleinsider.com!
I think I may need more guidance on how to identify this "interestingly named folder". It seems I can't proceed to the other steps until I identify the killer process. I looked in those two hidden folders you recommended as well as the Task Manager, but nothing really is catching my eye, although I am not too sure what to look for. Nothing appears with "av" or "419283".
Thanks again for the help.
That's not good. In all cases where I've personally, run across this malware, I've been running Firefox, which seems to have sand-boxed things.
Can you download an application called autoruns?
Once open, stay on the 'everything tab' and go to file > save.
Then can you email that file to me (PM me for an address).
I should be able to open it and see what's loaded, in terms of applications and drivers, then I should be able to point you in a meaningful direction.
If you can't open the autoruns (or autoruns.exe if you have 'show file extensions turned on) because the malware is closing it, rename it to explorer or explorer.exe
|
|
|
| |
|
|
|
 |
|
 |
|
Moderator Emeritus
Join Date: Apr 2005
Location: Cambridge, UK
Status:
Offline
|
|
Right, as you mentioned in your PM, I can see either the newer or a current infection:
Code:
c:\documents and settings\jzatz002\local settings\application data\995826023.exe
Please uncheck it in autoruns and confirm that it is deleted.
I have also noticed the following under the services tab:
Code:
userinit AV software \\.\globalroot\systemroot\system32\usеrinit.exe
userinit does not run as a service.
On my Windows box, that path displays the 'e' in userinit as a square, which means it is a special character of some sort, rather than a real e. Please uncheck that entry in autoruns.
To confirm it is not a real 'e' you can copy and paste that path into textedit and change the font to brush script. The 'e' does not change.
We then need to remove userinit from
Code:
C:\Windows\system32
, the fake one, not the real one!
I can't tell how it will look on your system, hopefully like this:
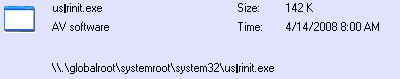
If you can sort those 2 items, see if things are running any better after a reboot. Then we need to look into running tdsskiller.
|
|
|
| |
|
|
|
 |
|
 |
|
Administrator  Join Date: Apr 2001
Location: San Antonio TX USA
Status:
Offline
|
|
|
|
 Glenn -----OTR/L, MOT, Tx
Glenn -----OTR/L, MOT, Tx
|
| |
|
|
|
 |
|
 |
|
Senior User
Join Date: Apr 2003
Status:
Offline
|
|
I have terminated the process 995826023.exe and deleted that file. However this was the one that just showed up today. The original virus from yesterday was still very much active even after removing 995826023.exe.
I unchecked the userinit file in autoruns. I found the fake userinit file by searching for "us?rinit", deleted it, rebooted, and the wallpaper/popups no longer appear! However, when I restored permissions on Mcafee and Malwarebytes, the two programs subsequently terminated again, so there is still something on my machine, I believe...
What is the next step? Thanks
|
|
|
| |
|
|
|
 |
|
 |
|
Moderator Emeritus
Join Date: Apr 2005
Location: Cambridge, UK
Status:
Offline
|
|
I'd now suggest you download and run Process Explorer.
If you enable the 'image path' column, you can see where applications are running from.
What I'm looking for is svchost.exe running from somewhere other than
Code:
C:\windows\system32
|
|
|
| |
|
|
|
 |
|
 |
|
Senior User
Join Date: Apr 2003
Status:
Offline
|
|
All of them are in that directory and highlighted red except for one, which is highlighted blue:
\\.\globalroot\Device\svchost.exe\svchost.exe
|
|
|
| |
|
|
|
 |
|
 |
|
Moderator Emeritus
Join Date: Apr 2005
Location: Cambridge, UK
Status:
Offline
|
|
Intriguing.
Kill and move that to the recycle bin.
Is there anything else running from?
\\.\globalroot\ ?
|
|
|
| |
|
|
|
 |
|
 |
|
Senior User
Join Date: Apr 2003
Status:
Offline
|
|
Originally Posted by seanc 
Intriguing.
Kill and move that to the recycle bin.
Is there anything else running from?
\\.\globalroot\ ?
Where can I find the directory to delete the file after I kill the process?
What's the next step after that?
Thanks for the continued help...
|
|
|
| |
|
|
|
 |
|
 |
|
Moderator Emeritus
Join Date: Apr 2005
Location: Cambridge, UK
Status:
Offline
|
|
If you right click on the process, there should be an option to show the file in explorer.
|
|
|
| |
|
|
|
 |
|
 |
|
Senior User
Join Date: Apr 2003
Status:
Offline
|
|
Originally Posted by seanc 
If you right click on the process, there should be an option to show the file in explorer.
That option does not appear in the popup menu. When I select properties, it shows the current directory as C  Documents and Settings\[user], but there is no directory inside my user folder named "Device" or svchost or a file called svchost.exe. I currently have explorer showing hidden/system files, etc.
|
|
|
| |
|
|
|
 |
|
 |
|
Moderator Emeritus
Join Date: Apr 2005
Location: Cambridge, UK
Status:
Offline
|
|
Can you run through this thread over on the Malwarebytes forums?
Rootkits with \\?\globalroot\Device\__max++>\ paths - Malwarebytes Forum
Do you see the DLL files it mentioned?
I have to say, this is where my suggestions run out, until I can get hold of an infected machine. I've not tackled any infections to do with \\.\globalroot paths.
Any idea how you contracted this nasty?
|
|
|
| |
|
|
|
 |
|
 |
|
Senior User
Join Date: Apr 2003
Status:
Offline
|
|
Originally Posted by seanc 
Can you run through this thread over on the Malwarebytes forums?
Rootkits with \\?\globalroot\Device\__max++>\ paths - Malwarebytes Forum
Do you see the DLL files it mentioned?
I have to say, this is where my suggestions run out, until I can get hold of an infected machine. I've not tackled any infections to do with \\.\globalroot paths.
Any idea how you contracted this nasty?
I am not sure I understand anything that link is saying, haha. Do you happen to know how I can find these DLLs?
When I do a search for "svchost.exe":, it shows 1 in system32 and the other in system32\dllcache
Should I kill the process and remove the one in dllcache?
|
|
|
| |
|
|
|
 |
|
 |
|
Moderator Emeritus
Join Date: Apr 2005
Location: Cambridge, UK
Status:
Offline
|
|
Nope, both are *possibly* genuine, at least they're in use. Deleting could be a bad idea.
Have a look in
Code:
C:\windows\system32\
for eventlog.dll and logevent.dll
How big are the files? Are they both there?
|
|
|
| |
|
|
|
 |
|
 |
|
Senior User
Join Date: Apr 2003
Status:
Offline
|
|
Originally Posted by seanc 
Nope, both are *possibly* genuine, at least they're in use. Deleting could be a bad idea.
Have a look in
Code:
C:\windows\system32\
for eventlog.dll and logevent.dll
How big are the files? Are they both there?
eventlog is 55KB. logevent is nowhere to be found. Therefore, it doesn't look like the exact same issue as that poster.
Should I still kill that one svchost?
What the heck is Win32kDiag and GMER?
|
|
|
| |
|
|
|
 |
|
 |
|
Moderator Emeritus
Join Date: Apr 2005
Location: Cambridge, UK
Status:
Offline
|
|
Try killing that particular svchost first, see what happens.
GMER is a program that will scan for rootkits. Might be worth running.
Not sure what Win32kDiag is.
|
|
|
| |
|
|
|
 |
|
 |
|
Senior User
Join Date: Apr 2003
Status:
Offline
|
|
Originally Posted by seanc 
Try killing that particular svchost first, see what happens.
GMER is a program that will scan for rootkits. Might be worth running.
Not sure what Win32kDiag is.
I selected kill process, but it never went away...
|
|
|
| |
|
|
|
 |
|
 |
|
Senior User
Join Date: Apr 2003
Status:
Offline
|
|
When I try running GMER, I see a red line:
Service (*** hidden ***) [MANUAL] vbmac707
and then get a popup saying GMER has found rootkit activity, but why I click to Scan, the program shuts down.
Why I try running Win32kdiag, the only thing I get is: Cannot access C  WINDOWS\inf\1394.inf
I am totally at a loss. Any help is much appreciated. And if the creator of this malware is ever known, I hope someone kicks his face repeatedly with metal baseball cleats.
|
|
|
| |
|
|
|
 |
|
 |
|
Clinically Insane
Join Date: Dec 1999
Status:
Offline
|
|
I suggest Hiren's Boot CD. It includes a little program to burn the .iso to a CD. Boot from the CD, and it contains drivers for nearly all network controllers. Activate your network stack so you can get on the internet, then run the various anti-virus and anti-malware applications (I think one of them is specifically for Antivirus 2010), and it'll clean up your computer.
Also include Registry cleaners like Crap Cleaner.
|
|
"…I contend that we are both atheists. I just believe in one fewer god than
you do. When you understand why you dismiss all the other possible gods,
you will understand why I dismiss yours." - Stephen F. Roberts
|
| |
|
|
|
 |
|
 |
|
Moderator Emeritus
Join Date: Apr 2005
Location: Cambridge, UK
Status:
Offline
|
|
Download and burn the Kaspersky rescue CD, burn and run it.
I've been working on machine today with an unknown malware infection.
I cleaned it up enough to stop Avast! moaning, but like you, MBAM kept closing and I couldn't download some files.
Kept citing weerx.bak and a Trojan called Katie. I'll catch up with it tomorrow. When I left, the Kaspersky rescue CD had found one other nasty trojan.
|
|
|
| |
|
|
|
 |
|
 |
|
Administrator  Join Date: Apr 2001
Location: San Antonio TX USA
Status:
Offline
|
|
Both Hiren's an Kapersky will help a lot. Having a way to run the computer and access the drive without running Windows allows you to do all sorts of things-including excising malware. The advantage of Kapersky is that it runs the machine AND does antivirus repair. I'd keep both CDs handy, just in case.
|
 Glenn -----OTR/L, MOT, Tx
Glenn -----OTR/L, MOT, Tx
|
| |
|
|
|
 |
 |
|
 |
|
|
|
|
|
 
|
|
 |
Forum Rules
|
 |
 |
|
You may not post new threads
You may not post replies
You may not post attachments
You may not edit your posts
|
HTML code is Off
|
|
|
|
|
|
 |
 |
 |
 |
|
 |